24 Hour Technical Support & Seattle Computer Repair
support@seattlecomputer.repair (206) 657-6685
We accept insurance coverage!
Virus, Spyware, & Malware Removal
- Details
- Tech Support by: Emerald City IT
- Support Field: Computer Repair and Tech Support
- Support Category: Virus, Spyware, & Malware Removal
- Details
- Tech Support by: Emerald City IT
- Support Field: Computer Repair and Tech Support
- Support Category: Virus, Spyware, & Malware Removal
- Details
- Tech Support by: Emerald City IT
- Support Field: Computer Repair and Tech Support
- Support Category: Virus, Spyware, & Malware Removal
A previous diary [1] described processing some local PCAP data with Zeek. This data was collected using tcpdump on a DShield Honeypot. When looking at the Zeek connection logs, the connection state information was unexpected. To help understand why, we will compare data from different locations on the network and process the data in a similar way. This will help narrow down where the discrepancies might be coming from, or at least where they are not coming from. Some initial factors considered:
- Differences in capture commands between pfsense and local honeypot
- Firewall placed between pfsense and honeypot
- Resource constraints on honeypot
To start, let's take a look at a high level overview of the network and where data is collected.
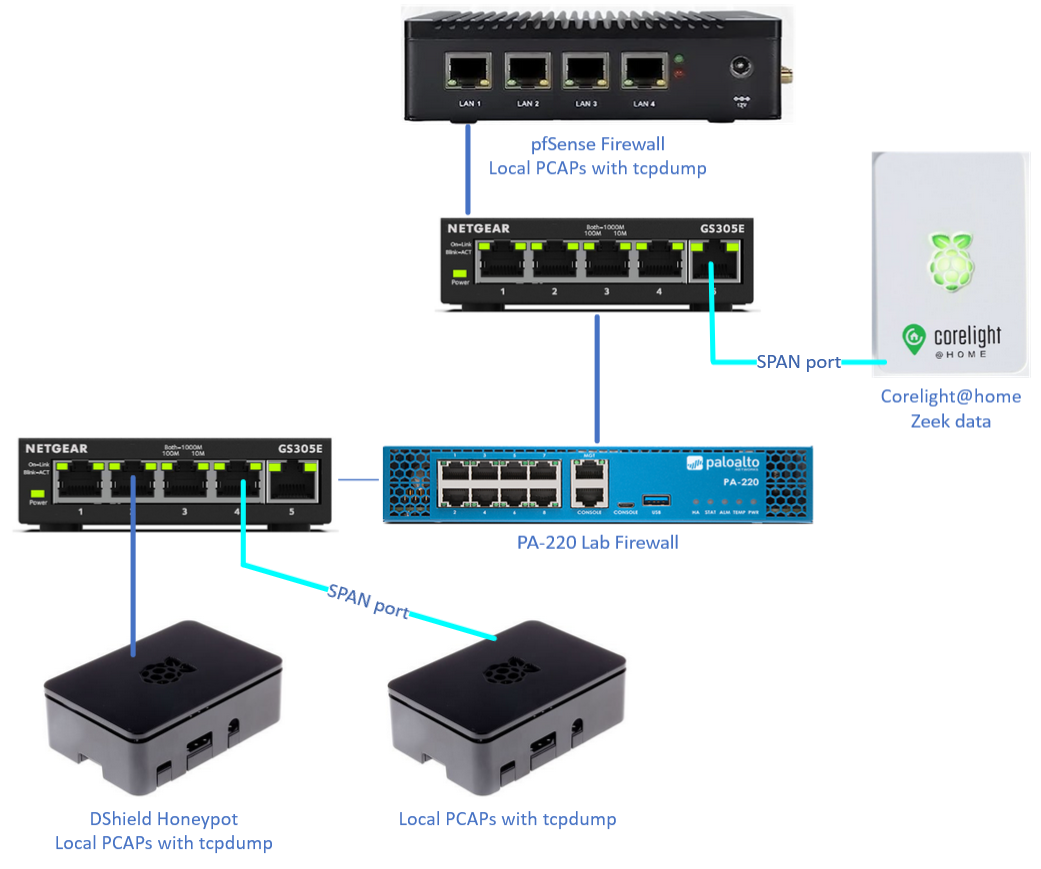
Figure 1: Layout of network and PCAP/Zeek data capture points
There are four locations currently collecting some kind of network data that can be used for comparisons. To help with the investigation, I added a switch with a SPAN [2] port and another Raspberry Pi to collect PCAP data for the honeypot. Our data collectors:
- pfsense - full PCAP for any ingress or egress traffic from the network
- Corelight@home [3] - Zeek data collection for any ingress or egress traffic from the network using a SPAN port
- DShield Honeypot - full PCAP for any ingress or egress traffic from the honeypot
- External PCAP collector for honeypot - full PCAP for any ingress or egress traffic from the honeypot using a SPAN port
With all four collectors in place it was just a matter of waiting to collect data to compare. Once the data was collected, the data was processed to compare all the Zeek data in a similar fashion. This mean limiting the data to only what came to and from the honeypot in addition to a specific timeframe.
# due to having larger and multiple PCAPs, data for the pfsense needed to be merged into one file mergecap *.pcap* -w combined.pcap # tshark was used to extract data # # get data from 2/15/2023 6 AM - 12 PM (6 hours) # (frame.time >= "Feb 15, 2023 06:00:00") && (frame.time <= "Feb 15, 2023 12:00:00") # # get data to/from honeypot only # (ip.addr == 192.168.68.178) tshark -r "combined.pcap" -w extract.pcap -Y '(frame.time >= "Feb 15, 2023 06:00:00") \ && (frame.time <= "Feb 15, 2023 12:00:00") && (ip.addr == 192.168.68.178)' # process extracted data with Zeek /opt/zeek/bin/zeek -r extract.pcapWith the data collected and processed, all that's left is to compare the different data sources. First, we'll take a look at the different connection states seen in the Zeek logs. Note that the Corelight@home data is stored in JSON format so using the 'jq' utility will be of good use here.
# display unique connection states from Zeek logs and sort by count using zeek-cut cat conn.log | /opt/zeek/bin/zeek-cut conn_state | sort | uniq -c | sort -n # display unique connection states from Zeek logs and sort by count using jq # # process JSON data and select data with 'ts' between 2/15/23 6AM-12PM (UTC -6) # jq '(select(.ts >= "2023-02-15T12:00" and .ts <= "2023-02-15T18:00"))' # # process JSON data and select source or dest IP of honeypot (192.168.68.178) # jq '(select((."id.orig_h"=="192.168.68.178") or (."id.resp_h"=="192.168.68.178")))' # # process JSON data, select "conn_state" and sort by unique count # jq .conn_state | sort | uniq -c | sort -n cat conn_*.log | jq '(select(.ts >= "2023-02-15T12:00" and .ts <= "2023-02-15T18:00"))' | \ jq '(select((."id.orig_h"=="192.168.68.178") or (."id.resp_h"=="192.168.68.178")))' | \ jq .conn_state | sort | uniq -c | sort -n 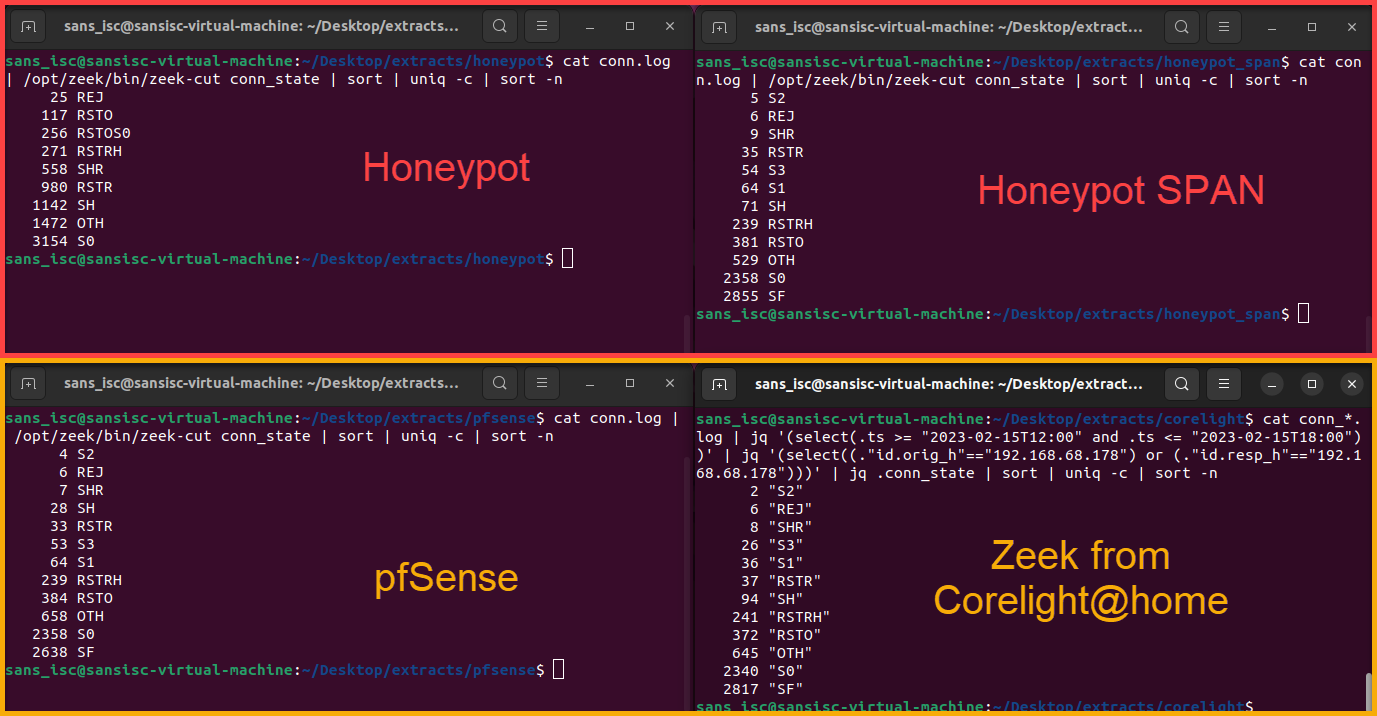
Figure 2: Comparison of four different network collection sources
| Connection State | Honeypot (Behind PA) | Honeypot SPAN | pfSense | Corelight@home |
| S2 | 0 | 5 | 4 | 2 |
| REJ | 25 | 6 | 6 | 6 |
| SHR | 558 | 9 | 7 | 8 |
| S3 | 0 | 54 | 53 | 26 |
| S1 | 0 | 64 | 64 | 36 |
| RSTR | 980 | 35 | 33 | 37 |
| SH | 1142 | 71 | 28 | 94 |
| RSTRH | 271 | 239 | 239 | 241 |
| RSTO | 117 | 381 | 384 | 372 |
| OTH | 1472 | 529 | 658 | 645 |
| S0 | 3154 | 2358 | 2358 | 2340 |
| SF | 0 | 2855 | 2638 | 2817 |
| RSTOS0 | 256 | 0 | 0 | 0 |
Reviewing the data within the connection states shows that a lot of the data for the locally generated PCAPs on the honeypot are outliers when comparing the other network data locations. There are some other deviations within the other three "non-outlier" datasets and some of these are likely due to other services running internally or directly on those collectors.
Comparing the 'Weird' [4] logs also shows some interesting differences.
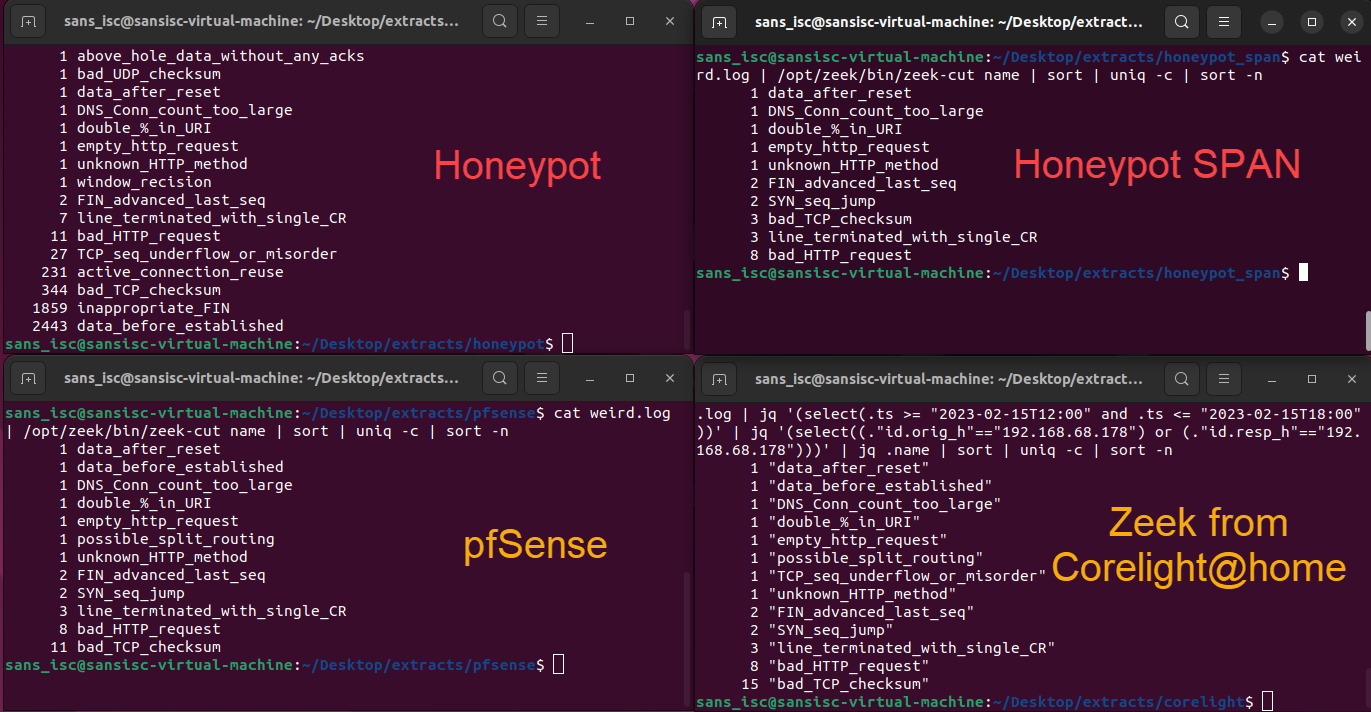
Figure 3: Zeek 'weird' log comparisons between different network location data sources
Just as seen within the Zeek connection state data, the local honeypot PCAP data collection is very different than the other three sources. Depending on the analysis being done with the network captures, the location of where that network data is collected can make a difference. This has also helped inform the previous hypotheses:
- Being behind another hardware firewall did not seem to make a significant difference
- Command used to collect PCAP data did not seem to make a significant difference
- Both tcpdump commands used on the Raspberry Pis were set up exactly the same with a daily cron task
Some important factors to keep in mind when setting up network data collections:
- Understand the network topology
- Do not host network services on data collection devices
- Test data collections from multiple locations and compare
- Avoid collecting duplicate data
[1] https://isc.sans.edu/diary/PCAP+Data+Analysis+with+Zeek/29530/
[2] https://www.gigamon.com/resources/resource-library/white-paper/to-tap-or-to-span.html
[3] https://github.com/corelight/raspi-corelight
[4] https://zeek.org/2019/11/13/what-is-weird-in-zeek/#:~:text=The%20most%20intriguing%20exception%20may,to%20avoid%2Fconfuse%20a%20sensor.
--
Jesse La Grew
Handler
- Details
- Tech Support by: Emerald City IT
- Support Field: Computer Repair and Tech Support
- Support Category: Virus, Spyware, & Malware Removal
Apple today released updates for all of its operating systems. The updates also apply for some of the older versions of iOS and macOS. For iOS/iPadOS 15, Apple now patched an already exploited vulnerability (CVE-2023-23529). Current operating systems received a patch for this vulnerability mid January.
Noteworthy is also that this is the first time, as far as I can recall, that we got a security update for the Studio Display firmware. Firmware updates were released before for the studio display, but they fixed non-security bugs.
| Studio Display Firmware Update 16.4 | Safari 16.4 | iOS 15.7.4 and iPadOS 15.7.4 | iOS 16.4 and iPadOS 16.4 | watchOS 9.4 | tvOS 16.4 | macOS Big Sur 11.7.5 | macOS Monterey 12.6.4 | macOS Ventura 13.3 |
|---|---|---|---|---|---|---|---|---|
| CVE-2023-27965 [important] Display A memory corruption issue was addressed with improved state management. An app may be able to execute arbitrary code with kernel privileges | ||||||||
| x | x | |||||||
| CVE-2023-27932 [moderate] WebKit This issue was addressed with improved state management. Processing maliciously crafted web content may bypass Same Origin Policy | ||||||||
| x | x | x | x | x | ||||
| CVE-2023-27954 [moderate] WebKit The issue was addressed by removing origin information. A website may be able to track sensitive user information | ||||||||
| x | x | x | x | x | x | |||
| CVE-2023-23541 [moderate] Accessibility A privacy issue was addressed with improved private data redaction for log entries. An app may be able to access information about a user?s contacts | ||||||||
| x | x | |||||||
| CVE-2023-27961 [moderate] Calendar Multiple validation issues were addressed with improved input sanitization. Importing a maliciously crafted calendar invitation may exfiltrate user information | ||||||||
| x | x | x | x | x | x | |||
| CVE-2023-23543 [moderate] Camera The issue was addressed with additional restrictions on the observability of app states. A sandboxed app may be able to determine which app is currently using the camera | ||||||||
| x | x | x | ||||||
| CVE-2023-27936 [important] CommCenter An out-of-bounds write issue was addressed with improved input validation. An app may be able to cause unexpected system termination or write kernel memory | ||||||||
| x | x | x | x | |||||
| CVE-2023-23537 [important] Find My A privacy issue was addressed with improved private data redaction for log entries. An app may be able to read sensitive location information | ||||||||
| x | x | x | x | x | ||||
| CVE-2023-27956 [important] FontParser The issue was addressed with improved memory handling. Processing a maliciously crafted image may result in disclosure of process memory | ||||||||
| x | x | x | x | x | ||||
| CVE-2023-27928 [moderate] Identity Services A privacy issue was addressed with improved private data redaction for log entries. An app may be able to access information about a user?s contacts | ||||||||
| x | x | x | x | x | x | |||
| CVE-2023-27946 [moderate] ImageIO An out-of-bounds read was addressed with improved bounds checking. Processing a maliciously crafted file may lead to unexpected app termination or arbitrary code execution | ||||||||
| x | x | x | x | |||||
| CVE-2023-23535 [important] ImageIO The issue was addressed with improved memory handling. Processing a maliciously crafted image may result in disclosure of process memory | ||||||||
| x | x | x | x | x | x | |||
| CVE-2023-27941 [important] Kernel An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. An app may be able to disclose kernel memory | ||||||||
| x | x | |||||||
| CVE-2023-27969 [important] Kernel A use after free issue was addressed with improved memory management. An app may be able to execute arbitrary code with kernel privileges | ||||||||
| x | x | x | x | x | ||||
| CVE-2023-27949 [moderate] Model I/O An out-of-bounds read was addressed with improved input validation. Processing a maliciously crafted file may lead to unexpected app termination or arbitrary code execution | ||||||||
| x | x | x | ||||||
| CVE-2023-28182 [moderate] NetworkExtension The issue was addressed with improved authentication. A user in a privileged network position may be able to spoof a VPN server that is configured with EAP-only authentication on a device | ||||||||
| x | x | x | x | x | ||||
| CVE-2023-27963 [moderate] Shortcuts The issue was addressed with additional permissions checks. A shortcut may be able to use sensitive data with certain actions without prompting the user | ||||||||
| x | x | x | x | x | ||||
| CVE-2023-23529 [critical] *** EXPLOITED *** WebKit A type confusion issue was addressed with improved checks. Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. | ||||||||
| x | ||||||||
| CVE-2023-23540 [important] Apple Neural Engine The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges | ||||||||
| x | x | x | ||||||
| CVE-2023-27959 [important] Apple Neural Engine The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges | ||||||||
| x | ||||||||
| CVE-2023-27970 [important] Apple Neural Engine An out-of-bounds write issue was addressed with improved bounds checking. An app may be able to execute arbitrary code with kernel privileges | ||||||||
| x | ||||||||
| CVE-2023-23532 [important] Apple Neural Engine This issue was addressed with improved checks. An app may be able to break out of its sandbox | ||||||||
| x | x | |||||||
| CVE-2023-23527 [moderate] AppleMobileFileIntegrity The issue was addressed with improved checks. A user may gain access to protected parts of the file system | ||||||||
| x | x | x | x | x | x | |||
| CVE-2023-27931 [important] TCC This issue was addressed by removing the vulnerable code. An app may be able to access user-sensitive data | ||||||||
| x | x | x | x | |||||
| CVE-2023-23494 [moderate] CarPlay A buffer overflow was addressed with improved bounds checking. A user in a privileged network position may be able to cause a denial-of-service | ||||||||
| x | ||||||||
| CVE-2023-27955 [moderate] ColorSync The issue was addressed with improved checks. An app may be able to read arbitrary files | ||||||||
| x | x | x | x | |||||
| CVE-2023-23528 [important] Core Bluetooth An out-of-bounds read was addressed with improved bounds checking. Processing a maliciously crafted Bluetooth packet may result in disclosure of process memory | ||||||||
| x | x | |||||||
| CVE-2023-28181 [important] CoreCapture The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges | ||||||||
| x | x | x | x | |||||
| CVE-2023-27937 [moderate] Foundation An integer overflow was addressed with improved input validation. Parsing a maliciously crafted plist may lead to an unexpected app termination or arbitrary code execution | ||||||||
| x | x | x | x | x | x | |||
| CVE-2023-23526 [moderate] iCloud This was addressed with additional checks by Gatekeeper on files downloaded from an iCloud shared-by-me folder. A file from an iCloud shared-by-me folder may be able to bypass Gatekeeper | ||||||||
| x | x | |||||||
| CVE-2023-27929 [important] ImageIO An out-of-bounds read was addressed with improved input validation. Processing a maliciously crafted image may result in disclosure of process memory | ||||||||
| x | x | x | x | |||||
| CVE-2023-27933 [important] Kernel The issue was addressed with improved memory handling. An app with root privileges may be able to execute arbitrary code with kernel privileges | ||||||||
| x | x | x | x | x | ||||
| CVE-2023-27943 [moderate] LaunchServices This issue was addressed with improved checks. Files downloaded from the internet may not have the quarantine flag applied | ||||||||
| x | x | |||||||
| CVE-2023-23525 [important] LaunchServices This issue was addressed with improved checks. An app may be able to gain root privileges | ||||||||
| x | x | |||||||
| CVE-2023-23523 [moderate] Photos A logic issue was addressed with improved restrictions. Photos belonging to the Hidden Photos Album could be viewed without authentication through Visual Lookup | ||||||||
| x | x | |||||||
| CVE-2023-27942 [important] Podcasts The issue was addressed with improved checks. An app may be able to access user-sensitive data | ||||||||
| x | x | x | x | x | ||||
| CVE-2023-28194 [moderate] Safari The issue was addressed with improved checks. An app may be able to unexpectedly create a bookmark on the Home Screen | ||||||||
| x | ||||||||
| CVE-2023-28178 [important] Sandbox A logic issue was addressed with improved validation. An app may be able to bypass Privacy preferences | ||||||||
| x | x | x | ||||||
| CVE-2022-26702 [important] AppleAVD A use after free issue was addressed with improved memory management. An application may be able to execute arbitrary code with kernel privileges | ||||||||
| x | ||||||||
| CVE-2023-27951 [moderate] Archive Utility The issue was addressed with improved checks. An archive may be able to bypass Gatekeeper | ||||||||
| x | x | x | ||||||
| CVE-2023-23534 [important] Carbon Core The issue was addressed with improved checks. Processing a maliciously crafted image may result in disclosure of process memory | ||||||||
| x | x | |||||||
| CVE-2023-27935 [critical] dcerpc The issue was addressed with improved bounds checks. A remote user may be able to cause unexpected app termination or arbitrary code execution | ||||||||
| x | x | x | ||||||
| CVE-2023-27953 [moderate] dcerpc The issue was addressed with improved memory handling. A remote user may be able to cause unexpected system termination or corrupt kernel memory | ||||||||
| x | x | x | ||||||
| CVE-2023-27958 [moderate] dcerpc The issue was addressed with improved memory handling. A remote user may be able to cause unexpected system termination or corrupt kernel memory | ||||||||
| x | x | x | ||||||
| CVE-2023-23514 [important] Kernel A use after free issue was addressed with improved memory management. An app may be able to execute arbitrary code with kernel privileges | ||||||||
| x | x | x | ||||||
| CVE-2023-28200 [important] Kernel A validation issue was addressed with improved input sanitization. An app may be able to disclose kernel memory | ||||||||
| x | x | x | ||||||
| CVE-2023-27962 [important] PackageKit A logic issue was addressed with improved checks. An app may be able to modify protected parts of the file system | ||||||||
| x | x | x | ||||||
| CVE-2023-23542 [important] System Settings A privacy issue was addressed with improved private data redaction for log entries. An app may be able to access user-sensitive data | ||||||||
| x | x | x | ||||||
| CVE-2023-28192 [important] System Settings A permissions issue was addressed with improved validation. An app may be able to read sensitive location information | ||||||||
| x | x | x | ||||||
| CVE-2023-0433 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim | ||||||||
| x | x | x | ||||||
| CVE-2023-0512 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim | ||||||||
| x | x | x | ||||||
| CVE-2023-27944 [important] XPC This issue was addressed with a new entitlement. An app may be able to break out of its sandbox | ||||||||
| x | x | x | ||||||
| CVE-2023-23538 [important] PackageKit A logic issue was addressed with improved checks. An app may be able to modify protected parts of the file system | ||||||||
| x | x | |||||||
| CVE-2023-23533 [important] Sandbox A logic issue was addressed with improved checks. An app may be able to modify protected parts of the file system | ||||||||
| x | x | |||||||
| CVE-2023-27968 [important] AMD A buffer overflow issue was addressed with improved memory handling. An app may be able to cause unexpected system termination or write kernel memory | ||||||||
| x | ||||||||
| CVE-2022-43551 [moderate] curl Multiple issues were addressed by updating curl. Multiple issues in curl | ||||||||
| x | ||||||||
| CVE-2022-43552 [moderate] curl Multiple issues were addressed by updating curl. Multiple issues in curl | ||||||||
| x | ||||||||
| CVE-2023-27934 [critical] dcerpc A memory initialization issue was addressed. A remote user may be able to cause unexpected app termination or arbitrary code execution | ||||||||
| x | ||||||||
| CVE-2023-28180 [moderate] dcerpc A denial-of-service issue was addressed with improved memory handling. A user in a privileged network position may be able to cause a denial-of-service | ||||||||
| x | ||||||||
| CVE-2023-28190 [important] FaceTime A privacy issue was addressed by moving sensitive data to a more secure location. An app may be able to access user-sensitive data | ||||||||
| x | ||||||||
| CVE-2023-27957 [moderate] ImageIO A buffer overflow issue was addressed with improved memory handling. Processing a maliciously crafted file may lead to unexpected app termination or arbitrary code execution | ||||||||
| x | ||||||||
| CVE-2023-27952 [important] Safari A race condition was addressed with improved locking. An app may bypass Gatekeeper checks | ||||||||
| x | ||||||||
| CVE-2023-0049 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim | ||||||||
| x | ||||||||
| CVE-2023-0051 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim | ||||||||
| x | ||||||||
| CVE-2023-0054 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim | ||||||||
| x | ||||||||
| CVE-2023-0288 [moderate] Vim Multiple issues were addressed by updating to Vim version 9.0.1191. Multiple issues in Vim | ||||||||
| x | ||||||||
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
- Details
- Tech Support by: Emerald City IT
- Support Field: Computer Repair and Tech Support
- Support Category: Virus, Spyware, & Malware Removal

